A Practical Playbook for Technology Adoption in the Fire Service
The fastest way to improve community risk reduction (CRR) outcomes isn’t conducting one more inspection—it’s fixing the data you already rely on. Standardizing occupancy information with verified geospatial data sources, partnering with third-party force multipliers, and wiring updates back into your record management system (RMS) closes the loop from CRR to computer-aided dispatch (CAD). This guide distills a candid conversation among practitioners into concrete steps you can implement now.
Why This Matters—Now
If you’ve ever chased duplicate addresses like “123 N Main St.” versus “123 N. Main Street,” you already know that bad data is a silent budget killer. Jill Cotton, President of InspectionReportsOnline (IROL), described years of “bad data entry habits” that splinter occupancy records and erode confidence across systems. Her team moved to using verified sources and implemented guardrails so that contributors can change the name of a location without breaking the underlying address record. This approach ends the spiral of duplicate data and preserves audit trails.
Will Brocious, Deputy Chief at Charlottesville (VA) Fire Department, emphasized the operational reality: No department has unlimited staffing or budget. Without technology—and partners—you fall behind. Third-party help doesn’t replace your people; it multiplies them.
The Problem We Can Actually Solve
Inconsistent occupancy entries create duplicates and misroutes across RMS, inspection software, and downstream systems. Cotton’s approach enforces location integrity by locking down addresses while allowing safe edits to business names or contacts. High-change environments such as malls and big-box suites shift tenants monthly, making it difficult to keep up. Brocious noted the value of offset inspections—where the department and third-party partners alternate visits—so that sites are touched twice a year, keeping contact and system information fresher than traditional cycles.
Another challenge is orphaned buildings. When cities adopt validated geospatial data capture, they often discover thousands of occupancies missing from legacy databases. These new records have real implications for community risk reduction.
What Verified Geospatial Data Really Means
This isn’t just about using a map; it’s about creating a workflow that enforces accuracy. It starts with an authoritative basemap and jurisdictional boundary, so contributors know what’s inside your footprint and what isn’t. Immediate detection of duplicate data prompts users with “Did you mean this?” checks, preventing variants at the point of capture. Guardrails on edits allow name changes while blocking address mutations, preserving data lineage and auditability. Finally, secure identities and logins aren’t friction—they’re protection. You get what you pay (and sign in) for.
Cotton’s caution is clear: Open, crowdsourced tools are great for consumers but not for life safety. Pins can be moved by anyone, and sources can be wrong. Verified inputs and identity controls are nonnegotiable when data guides response.
Closing the Loop: From CRR to CAD
An unsung step is the work of the gatekeeper, the designated person who validates inbound updates so that they match your data model. From there, your RMS pushes authoritative changes to CAD and dispatch platforms. When a call drops, verified addresses and site intel are already in the response stack. That’s not back-office convenience; that’s life safety.
Virtual Isn’t Verification (but it can be useful)
Video walk-throughs kept work going during COVID-19 and remain handy for narrow fixes like confirming an exit sign. But a virtual walk-through is not a substitute for validated data about systems, addresses, or building conditions. Use it as a tool—not the source of truth.
A Field-Tested Adoption Road Map
Start by defining the problem before buying a solution. Inventory pain points such as duplicates, missing occupancies, out-of-date contacts, and RMS-to-CAD mismatches. Standardize your schema by locking down authoritative address fields while allowing safe edits to names and contacts. Appoint a gatekeeper to triage inbound third-party updates, enforce standards, and own the round trip into RMS and CAD.
Next, equip your remote sensors by training contractors and partners on understanding why precision matters and giving them a map-first interface with duplicate detection and clear jurisdiction boundaries. Integrate the stack so that accepted updates flow from your GIS to RMS and onward to CAD and dispatch. Pilot the process, measure results, and iterate. Track metrics such as duplicates prevented, new occupancies discovered, update-to-dispatch time, and the percentage of calls with verified locations.
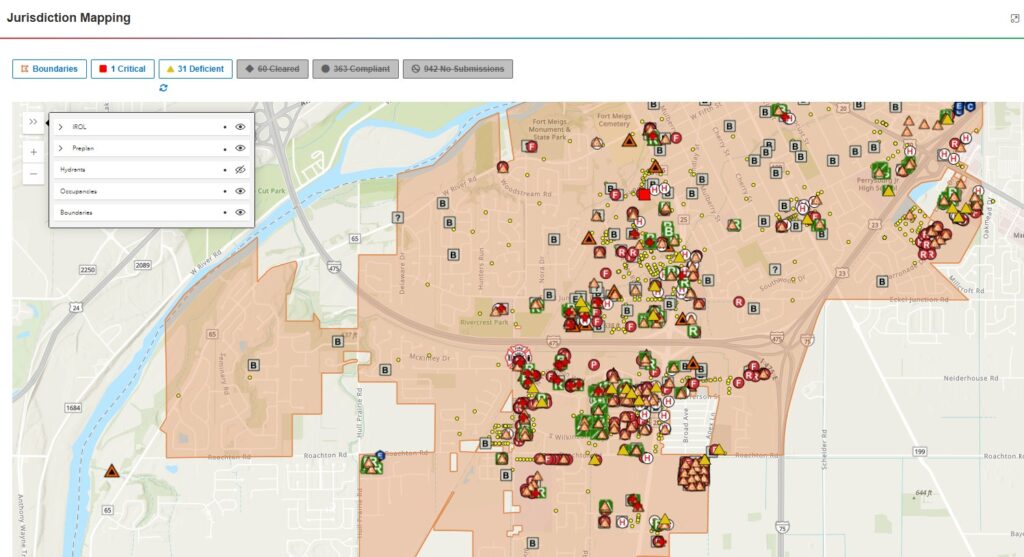
Finally, share the wins. Show responders and the community how verified data improves safety and reduces wasted responses, and celebrate partner contributions—their data is part of your mission.
What Success Looks Like
Success means duplicate data prevention at the point of entry, rapid discovery of missing inventory, and biannual touches on high-change occupancies by offsetting internal and partner inspections. It also means verified addresses in CAD before wheels roll, complete with current contacts and key system information.
Success also means applying governance to ensure the effective and efficient use of information technology and location intelligence to enable an organization to achieve its business goals. Understanding your geospatial strategy can help establish a vision and path for organizational success and help guide planning, prioritization, and the execution of projects.
Final Word
Technology adoption isn’t about the next shiny tool—it’s about trustworthy information moving where it must, when it must. Standardize the data, empower your partners, and wire the loop back to dispatch. Do that, and you’ll feel the difference at 2:00 a.m., not just in a dashboard.




